
In the 1700s a group of insiders from the London-based South Sea Company began spreading extravagant claims about the success and potential of the company as a trading giant in South America. Despite knowing that the company would never turn a profit, they were still able to lead many investors astray and artificially raise the price of their stock to record heights before its collapse shook the British economy.
This is one of the first recorded instances of a “pump-and-dump” scheme: a type of financial fraud usually performed by insiders that artificially inflates the price of a commodity through the spreading of misinformation.
Though this type of manipulation is by no means new, it has persisted to the present day. Pump-and-dumps have often been realized as a type of Microcap fraud, involving low priced ‘penny-stocks’, because they were deemed easier to manipulate. Recently, the scam has experienced its renaissance in the cryptocurrency space whose mostly unregulated nature made it an attractive target for nefarious actors who would seek to prey on the misinformed.
Pump-and-dumps often follow a predictable form (Figure 1), with three main stages. The accumulation phase occurs when a bad actor purchases a commodity at a relatively low price. This is followed by the pump phase, which artificially increases the demand (and thus the price) for the commodity. Lastly, the dump usually begins when the actors who bought during the accumulation phase begin to sell their holdings, causing the price to slip.
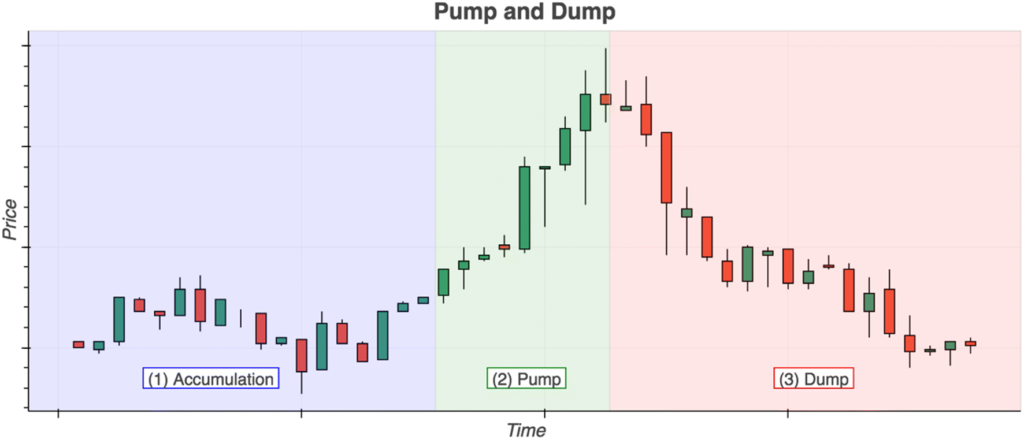
Our research noted that the timescale of modern pump-and-dump schemes has shortened, with many pumps lasting only seconds to minutes before the peak is reached.
Our research found that many cryptocurrency pump-and-dump groups organize themselves via online chat rooms such as Telegram and Discord. These scams are publicly accessible and anyone can participate, though the potential for profit seems to vary, since the pumps often only last a short amount of time making it difficult to predict the peak.
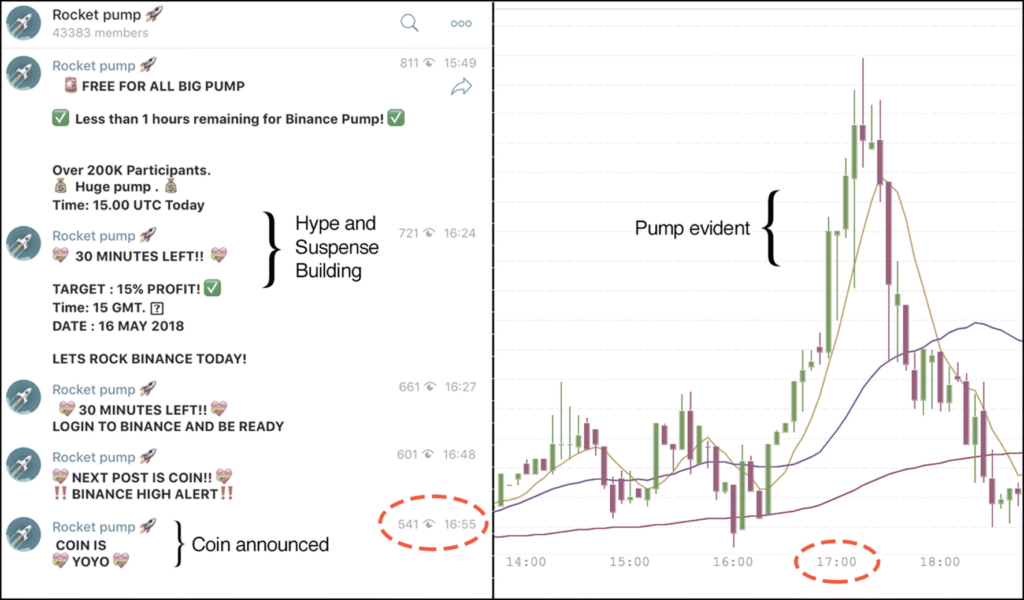
Typically, a group will choose a coin to be pumped and then announce that a pump will take place on a particular date, without specifying the coin. When the designated time comes, the coin to pump will be announced and users will scramble to purchase as quickly as possible (Figure 2).
Members of pump-and-dump groups are encouraged to spread the announced coin as the next big thing, for example on social media. This is intended to fool naive investors by exploiting their fear-of-missing-out on the next big investment. This presents a clear opportunity for insiders to use their foreknowledge of what coin is going to be pumped in order to secure profit, as they can buy it beforehand and then sell at the peak.
Findings of the study
Our research noted that as a result of the shift towards more real-time tactics employed by pump-and-dump actors (i.e. chat rooms vs. e-mail), the timescale of modern pump-and-dump schemes has correspondingly shortened, with many pumps lasting only seconds to minutes before the peak is reached.
A computational approach to detecting these schemes was investigated in our paper. We utilized a basic anomaly detection approach to detect unusual price and volume spikes in the data that are often seen during pump-and-dump schemes. This approach is necessary for any future large-scale detection work on cryptocurrency pump-and-dumps, as there are thousands of markets across many exchanges: reviewing them all by hand is not feasible.
We found that similarly to the traditional penny-stock market variant, the cryptocurrencies most vulnerable to this type of attack were the less popular ones with a low-market cap. This is due to their low liquidity making them easier to manipulate. We also found that around 30% of the cryptocurrency pairs we analyzed accounted for about 80% of the exhibited pump-and-dump activity.
There is minimal academic research regarding cryptocurrency pump-and-dumps, thus our research aimed to synthesize traditional economic literature with cryptocurrencies, and form a basis for future research.
From a crime science perspective we are interested in how these schemes take place, so that we can better understand how to implement preventative measures. Developing a computational approach to detecting these schemes, and learning from the observed patterns, is one step towards the goal of prevention.
Comments